以色列间谍软件'Graphite'疑在新加坡使用
新加坡服务器频成间谍软件部署据点

来自六个国家的组织或实体疑似利用名为“Graphite”的以色列间谍软件,从WhatsApp等通讯应用中窃取数据。
多伦多大学人权研究实验室“公民实验室”(The Citizen Lab)的报告显示,使用该软件的国家包括澳大利亚、加拿大、塞浦路斯、丹麦、以色列和新加坡。
这一披露距Meta旗下WhatsApp声明已近两月。该公司曾通报约90名记者与公民社会成员,称其成为“Graphite”的攻击目标,而这些攻击已于2024年12月被成功阻断。
间谍软件开发者是谁?
“Graphite”由以色列公司Paragon Solutions研发。该公司成立于2019年,创始人包括前总理埃胡德·巴拉克(Ehud Barak)和以色列国防军8200信号情报部队前指挥官埃胡德·施内尔松(Ehud Schneorson)。这款监控工具能从WhatsApp等即时通讯应用中提取敏感数据。
Paragon宣称其产品旨在协助政府及执法机构捕捉犯罪分子与恐怖分子。
与NSO集团臭名昭著的“飞马”(Pegasus)软件——可完全劫持手机——不同,“Graphite”据称仅专注于窥探WhatsApp或Signal等应用。
运作机制揭秘
“Graphite”技术精妙绝伦,采用“零点击漏洞”发动攻击——用户无需点击可疑链接,仅安装WhatsApp便可能沦为猎物。
攻击者将目标用户拉入聊天群组并发送PDF文件。即使用户毫无动作,其WhatsApp仍会被悄然攻陷。
一旦得逞,“Graphite”能窃取聊天记录、追踪用户行踪甚至挖掘更多信息,而受害者却毫无察觉。
“公民实验室”与Meta(WhatsApp母公司)联手侦测并封堵此威胁,但此前意大利的受感染安卓设备已留下线索——如代号“BIGPRETZEL”——直指Paragon。苹果公司随后在iOS 18中修复了这一攻击路径。

间谍软件使用范围追踪
研究人员通过服务器与IP地址分析,绘制出“Graphite”的全球网络足迹,涉及澳大利亚、加拿大、塞浦路斯、丹麦、以色列及新加坡等地。
然而,使用VPN等代理服务器可能导致定位偏差。“公民实验室”指出:“由于结论基于DNS服务器的国家级定位,VPN及卫星互联网中转站等因素可能影响准确性。”
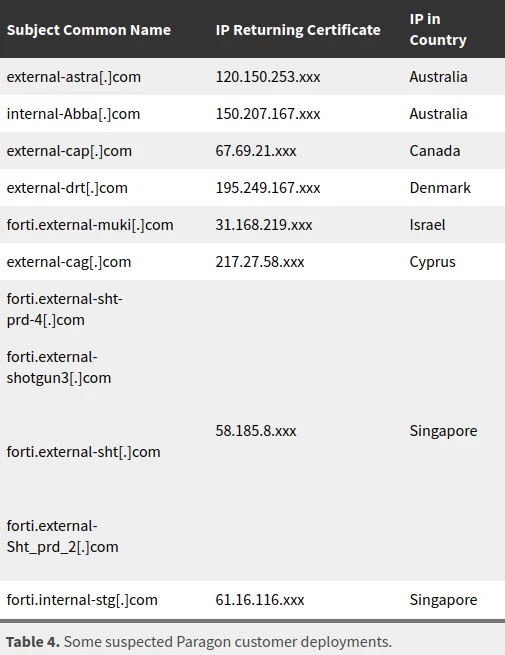
新加坡服务器频繁现身间谍软件部署
2018年,一次数据泄露暴露了疑似感染“飞马”间谍软件的5万多个电话号码。“公民实验室”调查发现,部分受感染手机位于英国、美国及新加坡。
当时,新加坡政府回应称知悉这些指控,但因未接获具体报告,无法核实其真实性。
2023年,“公民实验室”追踪到另一款以色列间谍软件“QuaDream”的疑似运营服务器,分布于保加利亚、捷克、匈牙利、加纳、以色列、墨西哥、罗马尼亚、新加坡、阿拉伯联合酋长国和乌兹别克斯坦等10国。
“QuaDream”可窃听通话、远程启用麦克风与摄像头、定位设备,并具备自毁功能,抹去一切痕迹,让用户无从察觉。
新加坡拒谈安全技术细节
根据《海峡时报》2023年报道,内政部兼国家发展部政务部长陈国明(Desmond Tan)于2022年被问及是否使用“QuaDream”时表示:“……肩负国家安全使命的机构必须倚靠多种情报能力,包括利用技术手段。”
“出于显而易见的原因,政府不能也不应公开讨论国家安全行动的具体细节或能力。”
内政部发言人强调,政府通常不会透露安全机构的工作方式:“我们的安全机构肩负维护新加坡安全、稳定与主权的重任。国家安全面临多元威胁,包括恐怖主义、外国颠覆、间谍活动及干预等。”
截至发稿,新加坡当局尚未对“Graphite”间谍软件事件置评。

