Israel's spyware 'Graphite' allegedly used in Singapore
Singapore servers commonly used to deploy Israeli spyware that harvests data from Whatsapp and other messaging apps. Singaporeans are not excluded from being targeted.

Organisations or entities from six countries likely used Israeli spyware named "Graphite" to harvest data from Whatsapp and other messaging apps.
According to a report by The Citizen Lab, a human rights research laboratory based at the University of Toronto, the countries where the spyware was used included Australia, Canada, Cyprus, Denmark, Israel, and Singapore.
The development comes nearly two months after Meta-owned WhatsApp said it notified around 90 journalists and civil society members that it said were targeted by Graphite. The attacks were disrupted in December 2024.
Who created the spyware?
Paragon Solutions, founded in 2019 by Ehud Barak and Ehud Schneorson, a former commander of signals intelligence agency Unit 8200 of the Israel Defense Force (IDF), is the maker of a surveillance tool called Graphite that's capable of harvesting sensitive data from instant messaging applications such as Whatsapp.
Paragon pitches its tools as helping governments and law enforcement agencies to catch criminals and terrorists.
Unlike infamous tools like NSO Group’s Pegasus, which can hijack your entire phone, Graphite supposedly sticks to snooping on apps like WhatsApp or Signal.
How it works
Graphite’s tech is slick - using a zero-click exploit. What this means is that you don’t need to click a shady link—just having WhatsApp installed could be enough.
The target user is added to a chat group and a PDF will be sent. Even without clicking or doing anything, the user's Whatsapp will be exploited.
Once in, Graphite can grab your chats, track your moves, and more, all while you’re none the wiser.
The Citizen Lab worked with Meta (WhatsApp’s parent company) to spot and block it, but not before infected Android phones in Italy left clues—like the codename “BIGPRETZEL”—tying it to Paragon.
Apple has since addressed the attack vector with the release of iOS 18.

Tracing where the spyware was used
Researchers mapped Graphite’s digital fingerprints—its servers and IP addresses—across the internet. What they found was a sprawling network touching countries like Australia, Canada, Cyprus, Denmark, Israel, and Singapore.
It is important to note, however, that the use of a proxy server such as a VPN, may introduce inaccuracies.
"As our findings are based on country-level geolocation of DNS servers, factors such as VPNs and satellite Internet teleport locations can introduce inaccuracies," the Citizen Lab said in 2018.
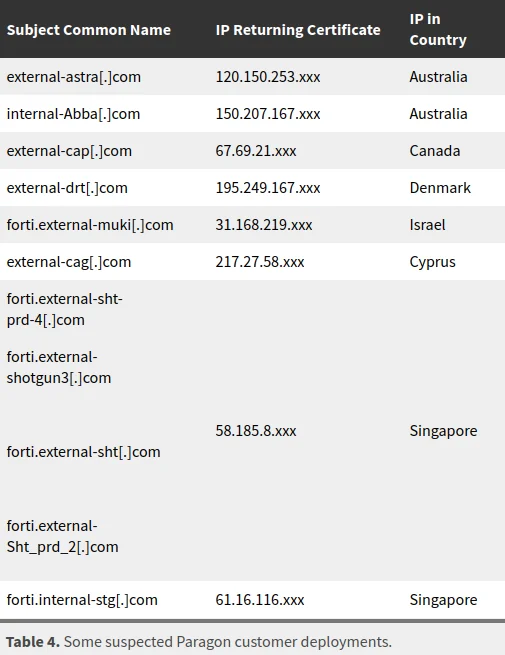
Singapore servers commonly used to deploy spyware
In 2018, a data leak containing more than 50,000 phone numbers were suspected to be infected with the spyware Pegasus, also sold by an Israeli surveillance company. An investigation conducted by The Citizen Lab found that some of the phones suspected to be infected by the Pegasus spyware were in the UK, US and Singapore.
Back then, the Singapore Government said it is aware of these claims but cannot verify them as no reports have been filed.
In 2023, the Citizen Lab identified also traced suspected operating servers for the QuaDream spyware - another Israeli-made spyware - to 10 countries – Bulgaria, the Czech Republic, Hungary, Ghana, Israel, Mexico, Romania, Singapore, the United Arab Emirates and Uzbekistan.
The QuaDream spyware allowed third parties to record audio from phone calls and the microphone, take pictures through the device's cameras, and track the device's location. It also contained a self-destruct feature that would wipe any traces left behind by the spyware, leaving users none the wiser.
Singapore does not discuss specifics of technologies used
According to a 2023 CNA report, Minister of State for Home Affairs Desmond Tan, when asked if Singapore employs the QuaDream spyware back in 2022, he said then: "...agencies charged with the mission of safeguarding national security necessarily have to rely on a range of intelligence capabilities, including harnessing technology.
“For obvious reasons, the Government cannot and should not discuss specifics on any operational aspects or capabilities regarding our national security.”
A spokesman for the Ministry of Home Affairs said the Government does not generally provide details of how security agencies carry out their work.
“Our security agencies’ task is to keep Singapore safe, secure and sovereign,” he said.
“Serious threats to national security are varied, and include terrorism, and foreign subversion, espionage and interference,” he added.
As of publishing time, Singapore's authorities have not commented on the Graphite spyware.

